Tailscale Funnel Is Going to Come in Handy!
Tailscale Funnel went into alpha a few days ago. It is a pretty nifty new feature for Tailscale. It lets you tunnel TLS connections from the Internet into your private Tailscale network. Isn’t that fun?
We are using Tailscale Funnel here at the Butter, What?! global media empire. In fact, if you are reading this blog post, then that means our Funnel is functioning correctly. How cool is that?!
What are we doing with our first Funnel?
We have some automation that pulls new commits from Gitlab, processes the new content through Jekyll, then uses rsync to publish those changes so you are able to read them.
This has been running on a loop for years. Our little script connects to Gitlab every few minutes looking for changes. If it finds changes, it goes to work. This does the job, but it feels inefficient. This isn’t the way to run a global media empire.
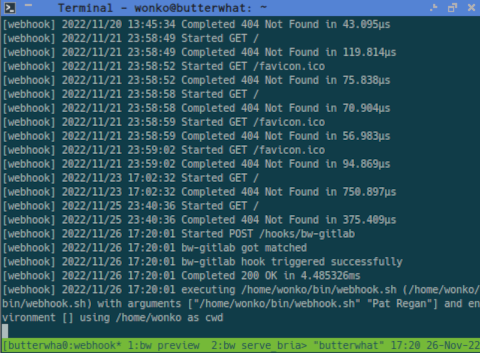
We wanted to make this more efficient, so we set up a Tailscale Funnel pointing to a webhook server. Whenever a commit is pushed, Gitlab connects to our little webhook server to let us know. Then our automation takes over.
Shoehorning this into our existing process was easy, but there are a few rough edges that could be handled better. It is a nice improvement, though, and it will definitely do the job for now!
You’re not telling us anything new! Wasn’t the post on your own blog enough?!
You are correct. I don’t think there’s going to be anything substantially new that I didn’t already mention in my post over at patshead.com. So why on Earth am I writing this stuff down again?!
I have a selfish reason. I want to see a new blog get published to Butter, What?! via the new Tailscale Funnel automation. Then I can go back to the original post and include a link proving that this all works.
I hope this excuse isn’t too thin, and I hope I don’t repeat myself too much!
I am even more excited about Tailscale’s new proxy than I am about the Fun Tunnels!
Holy potatoes! The new proxy server built into Tailscale is super handy! As far as I am concerned, the proxy server is the star of the new Tailscale update.
Adding HTTPS to a server is a pain. If you have a rack full of nginx servers, setting up certificates isn’t a big deal, but that is far from what I have here on my Tailnet.
I have a Home Assistant server, an Octoprint server, a Seafile server, and a handful of OpenWRT routers. One of those runs nginx, one is basically an appliance, and another is very nearly an appliance. Do I want to have to read the documentation to figure out where the certs have to be set up for each of these servers? Heck, no!
wonko@octoprint:~$ sudo tailscale serve status
https://octoprint.humpback-rooster.ts.net (tailnet only)
|-- / proxy http://127.0.0.1:5000
wonko@octoprint:~$
It took me about three minutes to put a Tailscale proxy in front of my Octoprint server, and I probably spent half that time just upgrading Tailscale to the unstable branch to get support for the proxy server.
This means I now already know how to wrap any web server in HTTPS with Tailscale proxy. I can set this up in less time than it would take me just to figure out which web server software my machines are using, and that is awesome.
Conclusion
Tailscale Funnel is only in alpha. You have to request an invitation to try it out, and you’ll have to upgrade some of your Tailscale clients to the unstable packages to make it work. I assume a lot of things will change regarding Tailscale Funnel and the proxy as they head to beta and then on to a general release.
I expect most of those changes will be for the better. I am hoping that the Tailscale proxy becomes less restricted, because today you can only proxy services running on the same node as the client. It would be nice to be able to proxy web servers that won’t allow me to install Tailscale.
What do you think? Are you already using Tailscale Funnel? Are you as excited as I am about the new proxy server? Tell us about it in the comments, or stop by [the Butter, What?! Discord server][bwd] to chat with me about it!